Run Apis on an account that does not have interactive log-in rights
Introduction
It is fully possible to run Apis Foundation services on user’s that don’t have interactive login rights.
However, the requirements for user running Apis Foundation are:
- The user has local administrative rights.
- Log on as a batch job is allowed in local policy security settings.
- Log on as a service is allowed in local policy security settings.
Deny interactive logon for Apis Service Accounts
There are slight differences in how interactive logon is restricted, depending on the computer is member of domain or not, this is described in detail below.
Deny interactive logon when computer member of domain
- In Active Directory, create an OU such as “Deny Interactive Logon” for storing your Service Account Users
- Create a Security Group which will hold all the Service Account users. Call it something meaningful such “Denied Interactive Logon Users”
- Create the User to be used as a Service Account and give them the required rights - try and avoid giving Domain Admin where possible. Add information about what this service account is used for in the description field.
- Move this user to the “Deny Interactive Logon” OU and add to the “Denied Interactive Logon Users” group. Open Group Policy Management. Create a new GPO and link it at the Domain level. Again, call it something meaningful such as “Lab Service Accounts Deny Interactive Logon”
- Edit the Group Policy. Under Computer Configuration/ Windows Settings/Security Settings/Local Policies/User Rights Assignment
- Add the “Denied Interactive Logon Users” Security Group to “'Deny log on locally” and “Deny log on through Terminal Services”If “Log on as a batch job” and “Log on as a service” policies are defined add the “Denied Interactive Logon Users” group to these policies.
Deny interactive logon when computer stand alone, not member of domain
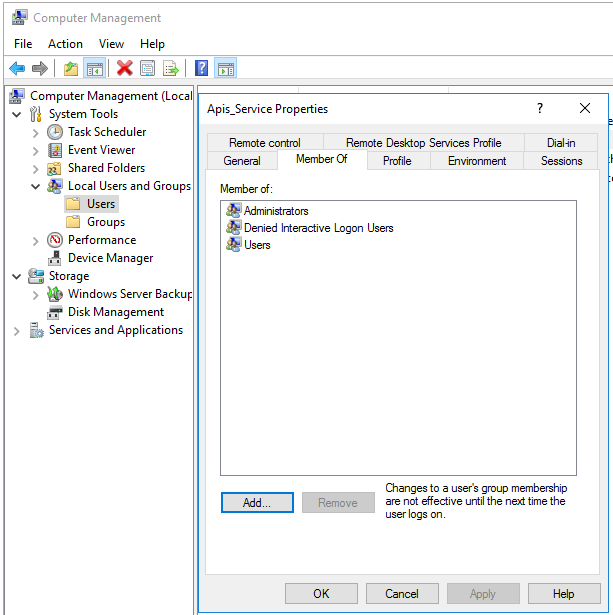
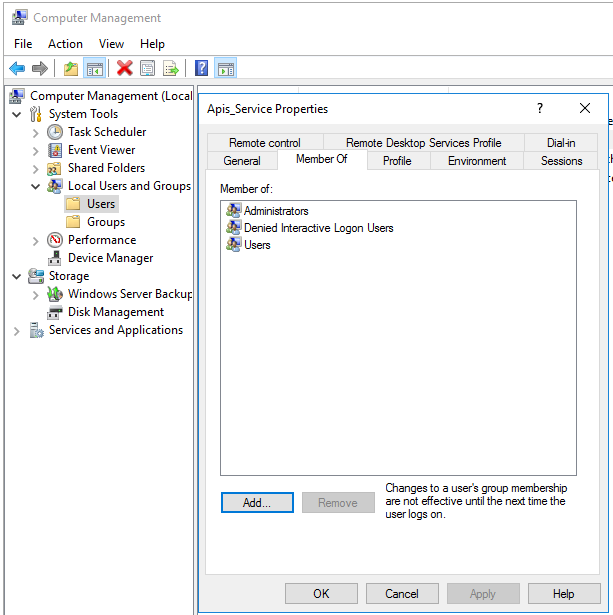
- Create a Group which will hold all the Service Account users. Call it something meaningful such “Denied Interactive Logon Users”
- Create the User to be used as a Service Account and give them the required rights. Add information about what this service account is used for in the description field.
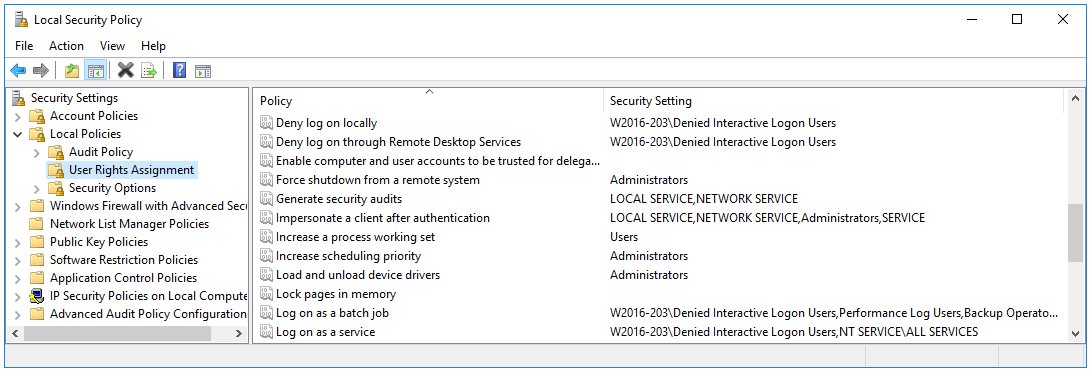
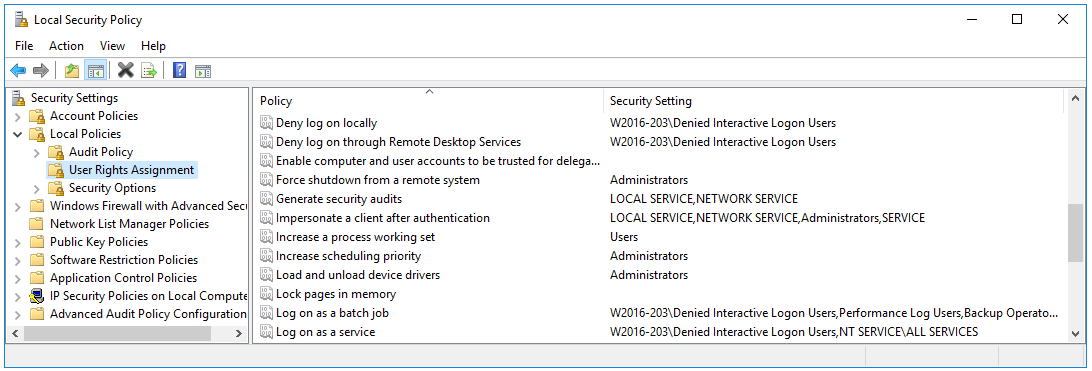
- Edit the Local Security Policy. Under Security Settings/Local Policies/User Rights Assignment
- Add the “Denied Interactive Logon Users” Group to “'Deny log on locally” and “Deny log on through Terminal Services
- Add the “Denied Interactive Logon Users” group to the “Log on as a batch job” and “Log on as a service” policies.